Services & Operational Workflows
Aussivo powers Web3-native DevOps — enabling developers to log in with wallets, activate decentralized infrastructure, and manage compute and storage on-chain with total transparency.
End-to-End Hosting Workflow
Here’s how Aussivo handles service provisioning — in 8 streamlined steps:
-
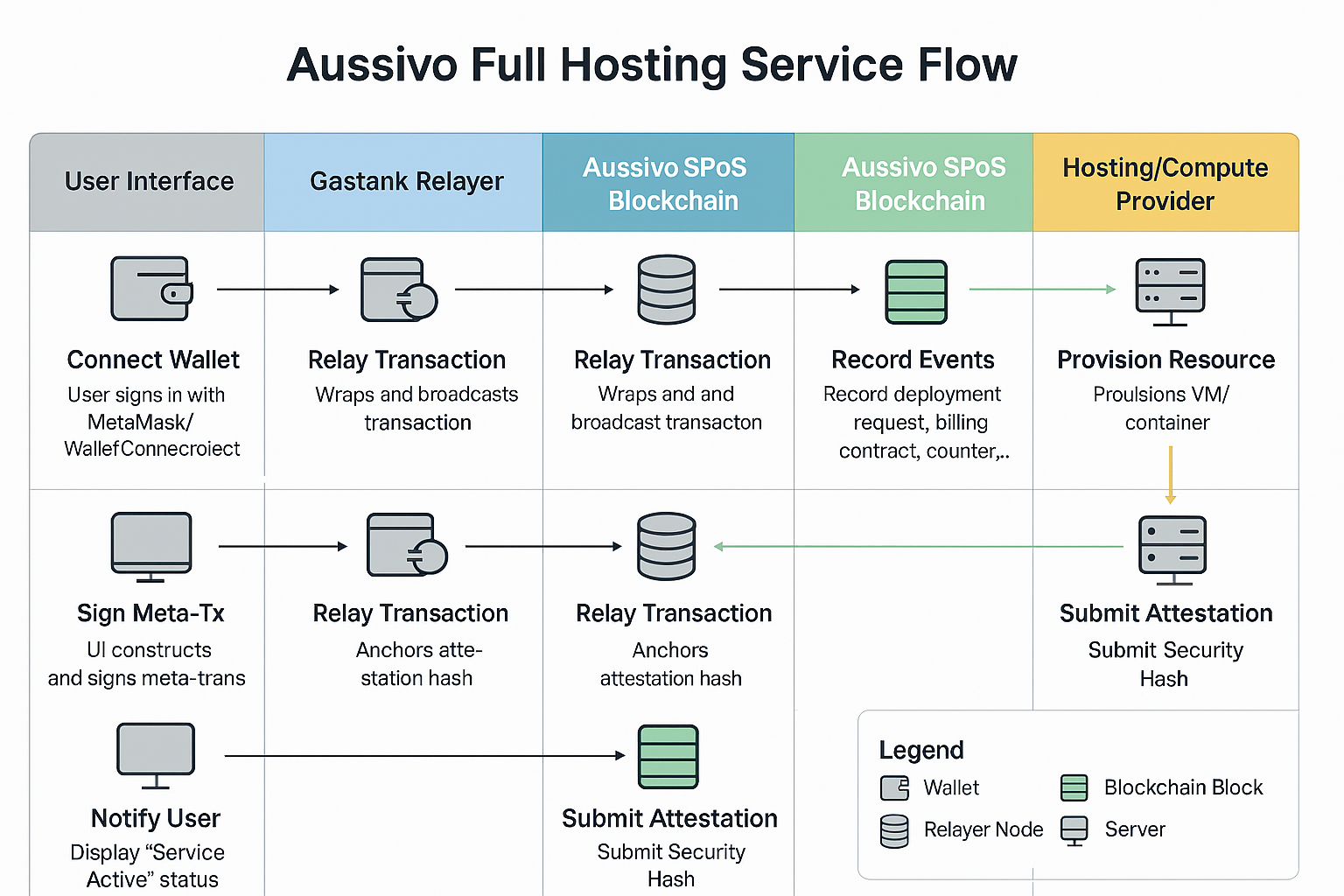
Wallet Login : Users log in using crypto wallets like Metamask or WalletConnect. No passwords — just secure wallet signatures.
-
Service Selection : Users choose from pre-configured templates for compute, storage, or full hosting setups. Custom parameters can be added.
-
Meta-Transaction Creation :
The system creates a signed meta-transaction with all selected options and instructions. -
Relayer Submission :
Aussivo’s Gastank relayer receives the meta-tx, wraps it into a blockchain-ready transaction, and submits it to the SPoS chain. -
Smart Contract Execution :
Smart contracts handle billing, trigger provisioning, and log usage events — all on-chain and fully auditable. -
Cloud Integration :
Aussivo’s orchestrator invokes APIs to launch resources — whether on Aussivo’s native data centers, AWS (with Nitro Enclave), or Alibaba Cloud. -
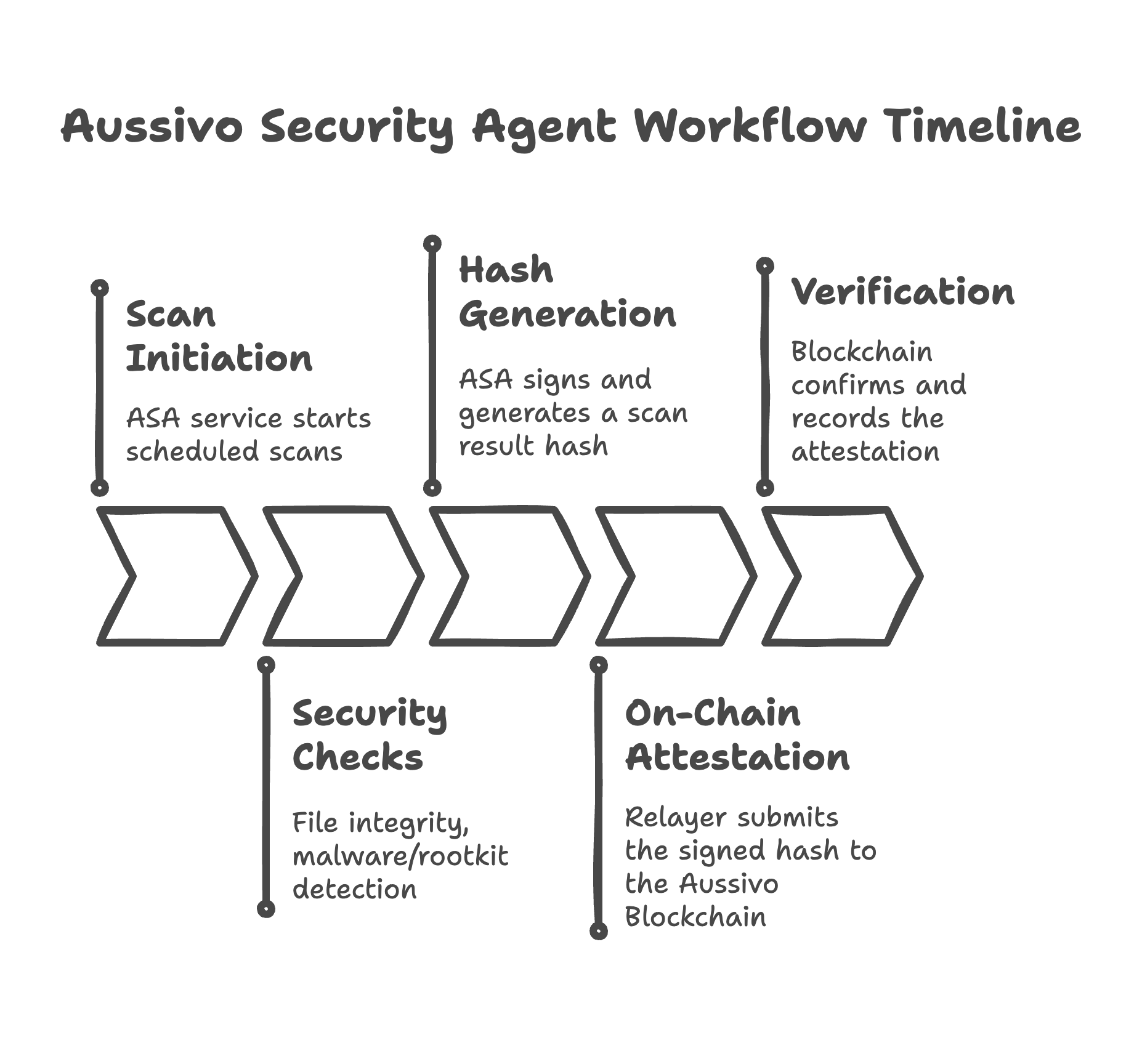
Security Agent Deployment :
The Advanced Security Agent (ASA) is auto-installed on new instances. It performs integrity scans and records results on-chain. -
Live Dashboard Monitoring :
Users can monitor everything in real time — from service activation and endpoints to billing, uptime, and security logs.
Security Agent (ASA) Tiers
| Functionality | Basic Tier | Enhanced Tier (Nitro Enclave) |
|---|---|---|
| Deployment | Runs as a VM-level software agent | Runs inside a Nitro Enclave with Trusted Launch |
| Security Checks | Malware, rootkits, file & network scans | All Basic checks + hardware-backed attestation |
| Key Protection | Encrypted inside the VM | Enclave-based tamper-proof key storage |
| On-Chain Anchoring | Relayer posts signed hash | Relayer posts enclave-signed, hardware-verified hash |
| Audit Verification | Signature integrity check on-chain | Hardware attestation verified by SPoS validators |
Simplified Data Flow
User → Wallet Login → Service Selection → Meta-Tx → Relayer → Blockchain → Cloud Instantiation → ASA Scan → Dashboard View