Introduction
an autonomous, blockchain-powered ecosystem delivering scalable compute, hosting, and digital services on demand.
1.Executive Summary
Aussivo is an intelligent blockchain layer that overlays existing cloud infrastructure to bring verifiable trust, auditability, and automation to modern cloud systems.
Powered by a Secure Proof-of-Stake (SPoS) consensus enhanced with zk-rollups, Aussivo achieves enterprise-grade scalability exceeding 15,000 TPS combining high throughput with strong cryptographic assurance.
What makes Aussivo stand out is its Gastank Protocol, which abstracts gas payments across chains. Users can submit transactions and pay fees in ASVO — they don't need the target chain's native gas token. Builders decide whether fees are charged to the user (default) or sponsored by the dApp. Aussivo itself does not sponsor transactions by default; Gastank simply provides the infrastructure (paymasters, relayers, and settlement) to make cross-chain gas seamless and auditable.
$ASVO powers staking, governance, compute verification, and now serves as the universal payment asset for Gastank, allowing users or dApps to pay cross-chain gas in ASVO, with settlement handled by Aussivo relayers and logged for audit.
Key Highlights
- Scalability: 15,000+ TPS with zk-rollup and sharding enhancements
- Gas Abstraction UX: Users can pay gas in $ASVO across supported chains — no native gas tokens needed
- Built-in Security: Hardware-based verification with Nitro Enclaves
- Smart Tokenomics: Deflationary $ASVO with burn mechanics
- Governance Ready: On-chain DAO and emergency override system (GateSeal)
2. The Problem We're Solving
Today's IT world relies on cloud and blockchain systems that often act like insurance plans with confusing fine print and hidden fees. Businesses struggle with unclear coverage, unexpected costs, and growing cyber risks.
Aussivo simplifies this by offering verifiable, blockchain-grade security and transparency, ensuring every deployment is provable, traceable, and auditable end to end.
2.1 Centralization & Lack of Transparency
- Untraceable Data Workflows: Enterprises can’t verify where their data came from or how it was processed
- Hidden Billing Models: Users struggle to understand or audit cloud billing
- Vendor Lock-In: Cloud platforms use proprietary APIs, limiting portability
2.2 Security Gaps & Audit Challenges
- No Verifiable Proofs: Logs and security events can be deleted or manipulated
- Complex Threats: Attackers exploit runtime and supply-chain vulnerabilities
- Lack of Real-Time Attestation: Security breaches are often detected too late
2.3 Barriers to Web3 Adoption
- High Gas & Cross-Chain Friction: Paying gas in multiple native tokens increases complexity and slows onboarding
- Fragmented Wallet Experience: End-users and developers still juggle different wallets and signing flows across chains, making UX inconsistent
- Cross-Chain Interoperability Gaps: Existing bridges and protocols remain slow and opaque; multi-chain execution lacks verifiable routing
Aussivo solves these challenges by merging cloud-level orchestration with blockchain-level verifiability.
With features like on-chain resource tracking, real-time security proofs, gas abstraction for multi-chain transactions, and streamlined wallet interactions, Aussivo empowers teams to deploy, secure, and scale decentralized systems confidently — without changing how users manage their own wallets or keys.
3. Our Solution
Aussivo's ecosystem is built on a modular, enterprise-grade architecture designed to eliminate the friction of both Web2 and Web3 infrastructure.
3.1 On-Chain Governance & Auditability
- Track Everything: Every virtual machine, container, or data file is logged as an on-chain transaction — capturing location, configuration, and runtime
- Auto Billing: Smart contracts trigger usage-based billing with real-time, verifiable invoices accessible to auditors and partners
3.2 Advanced Security Agent (ASA)
- Real-Time Proofs: Continuously verifies workloads, files, and configurations, converting them into on-chain cryptographic proofs
- Trusted Execution Environments: Operates within secure enclaves (e.g., Nitro Enclaves, Azure Confidential VMs, SGX) to ensure tamper-proof attestation
- Immutable Audit Trails: Anchors every verification event to Aussivo's blockchain, enabling regulators and enterprises to verify cloud trust independently
3.3 Secure zk-Rollup Layer
- Massive Scale: Bundles hundreds of transactions into a single zk-proof, reducing fees and congestion
- Instant Finality: zk-proofs are verified on Aussivo's mainnet within seconds, achieving Layer-1-level finality
3.4 Gastank Protocol & Relayer Network
- Unified Gas Abstraction: Developers and users can pay gas in $ASVO across supported EVM and non-EVM chains — no need for native gas tokens
- Flexible Fee Model: Aussivo does not sponsor gas fees by default. Each dApp or enterprise decides whether to charge users in ASVO or sponsor gas on their behalf
- Meta-Transactions: Users simply sign an intent; Gastank relayers handle native gas settlement and anchor proofs on Aussivo for transparency
- Cross-Chain Smart Routing: Relayers automatically choose the optimal route for lowest latency and cost across supported chains
3.5 One-Click AI Marketplace
- Pre-Built Templates: Deploy ERP, LMS, AI inference, or DeFi modules in minutes
- Fast Setup: Use Infrastructure-as-Code and pre-audited templates to go live instantly
- Benchmarked & Curated: Only high-performance, ASA-verified services make it to the marketplace
3.6 Deflationary Token – $ASVO
- Automatic Burns: A portion of each transaction is burned via an EIP-1559-style model, reducing supply over time
- Gas Utility Expansion: $ASVO also serves as the universal gas payment asset within Gastank, enabling seamless cross-chain interactions
- DAO-Led Evolution: $ASVO holders vote on protocol upgrades, fee structures, and governance proposals
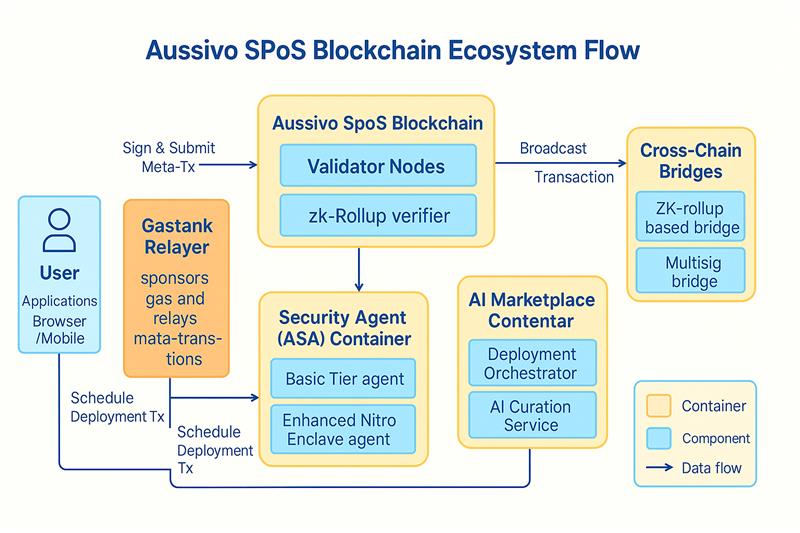
4. Architecture Overview
4.1 SPoS Blockchain Layer
- Secure Proof-of-Stake (SPoS): Validators stake $ASVO to secure and validate the network
- Fast & Fair: Leader selection via Verifiable Random Function (VRF) ensures fairness
- High Performance: Supports 15,000+ TPS with zk-rollups and sharding scalability
4.2 Core System Components
| Component | Function |
|---|---|
| Validator Nodes | Stake $ASVO, validate blocks, verify zk-proofs, and finalize transactions |
| Gastank Relayers | Handle meta-transactions, convert ASVO to native gas, and settle cross-chain fees per dApp policy |
| Security Agent (ASA) | Runs continuous audits and anchors verified logs on-chain |
| AI Marketplace | Deploys pre-built smart services via Infrastructure-as-Code templates |
| Cross-Chain Bridges | Connects Aussivo with EVM and non-EVM chains using zk and multisig bridges |
Component Diagram